Different things can be done to reduce the detection of the malware.
Binary Signature
Signing the executable helps a lot to reduce detection. Well-known certification authorities sell code certificates but they are very expensive.
If it is not possible to obtain a trusted code certificate, it should be done with self-signed ones.
Self-Signed Certificate
Here are the steps to follow to create a self signed CA, create the certificate and sign the binary:
#Self signed CA:
makecert -r -pe -n "CN = Microsoft Root Certificate Authority 2010,O = Microsoft Corporation,L = Redmond,S = Washington,C = US" -ss CA -sr CurrentUser -a sha256 -cy authority -sky signature -sv CA.pvk CA.cer
#Self signed cert:
makecert -pe -n "CN=Microsoft Windows Production PCA 2011,O = Microsoft Corporation,L = Redmond,S = Washington,C = US" -a sha256 -cy end -sky signature -eku 1.3.6.1.5.5.7.3.3,1.3.6.1.4.1.311.10.3.24,1.3.6.1.4.1.311.10.3.6 -ic CA.cer -iv CA.pvk -sv SPC.pvk SPC.cer
#Convert to PFX:
pvk2pfx -pvk SPC.pvk -spc SPC.cer -pfx SPC.pfx
# Sign binary:
signtool sign /v /fd SHA256 /f SPC.pfx binary.exe
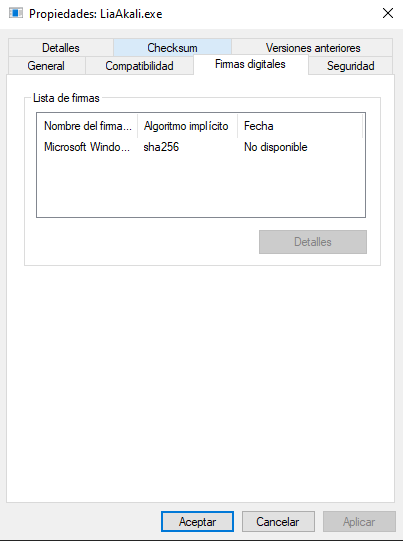
Binary Details
The more you can get your file legitimate, higher chances there are to evade the defenses.
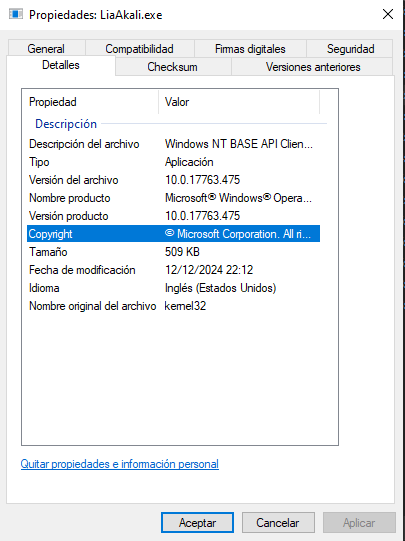
We can add some info on the details of our binary. To do that we need to add a resource file on our project.
- resources.rc
1 VERSIONINFO
FILEVERSION 10,0,17763,475
PRODUCTVERSION 10,0,17763,475
FILEOS 0x40004
FILETYPE 0x2
{
BLOCK "StringFileInfo"
{
BLOCK "040904B0"
{
VALUE "CompanyName", "Microsoft Corporation"
VALUE "FileDescription", "Windows NT BASE API Client DLL"
VALUE "FileVersion", "10.0.17763.475 (WinBuild.160101.0800)"
VALUE "InternalName", "kernel32"
VALUE "LegalCopyright", "\xA9 Microsoft Corporation. All rights reserved."
VALUE "OriginalFilename", "kernel32"
VALUE "ProductName", "Microsoft\xAE Windows\xAE Operating System"
VALUE "ProductVersion", "10.0.17763.475"
}
}
BLOCK "VarFileInfo"
{
VALUE "Translation", 0x0409 0x04B0
}
}
The resource file should be specified on compilation.
rc resources.rc
cvtres /MACHINE:x64 /OUT:resources.obj resources.res
cl.exe /nologo /Ox /MT /W0 /GS- /DNDEBUG /Tcrtnotes.cpp /link /OUT:rtnotes.exe /SUBSYSTEM:CONSOLE /MACHINE:x64 resources.obj
 Red Team Notes
Red Team Notes