Introduction to API Hooking
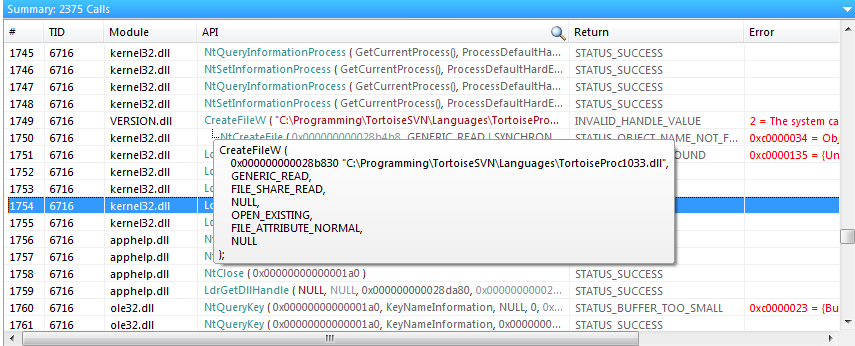
To find interesting calls to Windows API from a process we can use API Monitor.
Detour
Detour is a Windows framework that offers dynamic application of interception code at runtime. With detour we can create a dll which will be injected on the process we want to hook. We can use that lib to do API Hooking.
DetourTransactionBegin()DetourUpdateThread()DetourAttach()DetourDettach()
Once the hooked function is called, Detour will redirect the flow to our function. Usefull to log, modify or bypass some restrictions.
Code
Example of windows api hooking with Detour:
#include <stdio.h>
#include <windows.h>
#include "detours.h"
#pragma comment(lib, "user32.lib")
// pointer to original MessageBox
int (WINAPI * pOrigMessageBox)(HWND hWnd, LPCTSTR lpText, LPCTSTR lpCaption, UINT uType) = MessageBox;
BOOL Hookem(void);
BOOL UnHookem(void);
// Hooking function
int HookedMessageBox(HWND hWnd, LPCTSTR lpText, LPCTSTR lpCaption, UINT uType) {
printf("HookedMessageBox() called!\n");
pOrigMessageBox(hWnd, "TESTING WITH HOOKS", "RTNOTES", uType);
return IDOK;
}
// Set hooks on MessageBox
BOOL Hookem(void) {
LONG err;
DetourTransactionBegin();
DetourUpdateThread(GetCurrentThread());
DetourAttach(&(PVOID&)pOrigMessageBox, HookedMessageBox);
err = DetourTransactionCommit();
printf("MessageBox() hooked!\n", err);
return TRUE;
}
// Revert all changes to original code
BOOL UnHookem(void) {
LONG err;
DetourTransactionBegin();
DetourUpdateThread(GetCurrentThread());
DetourDetach(&(PVOID&)pOrigMessageBox, HookedMessageBox);
err = DetourTransactionCommit();
printf("Hook removed from MessageBox()\n", err);
return TRUE;
}
BOOL WINAPI DllMain(HINSTANCE hinst, DWORD dwReason, LPVOID reserved) {
switch (dwReason) {
case DLL_PROCESS_ATTACH:
Hookem();
break;
case DLL_THREAD_ATTACH:
break;
case DLL_THREAD_DETACH:
break;
case DLL_PROCESS_DETACH:
UnHookem();
break;
}
return TRUE;
}
 Red Team Notes
Red Team Notes